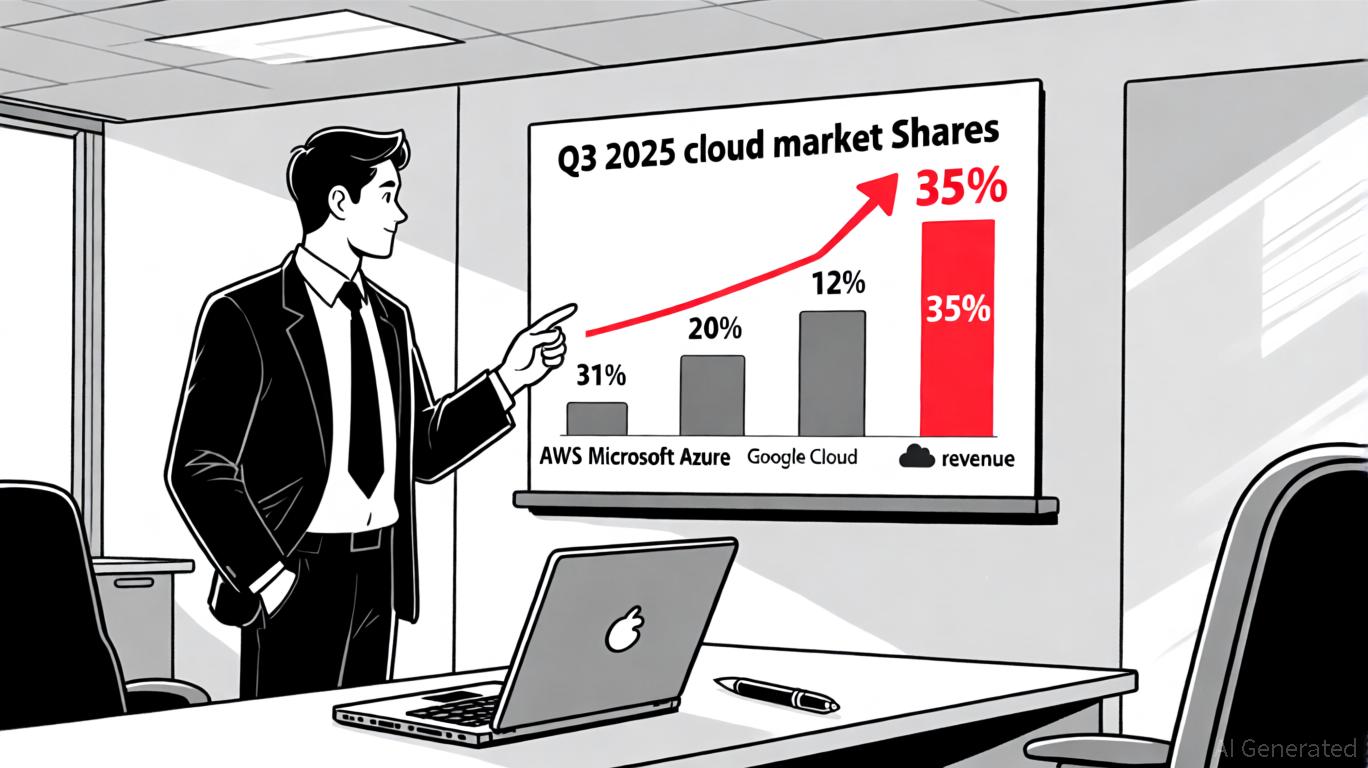
Unveiling Digital Transparency: How AMD Privacy View Changes the Game for Processor-Level Data Insights
Unveiling Digital Transparency: How AMD Privacy View Changes the Game for Processor-Level Data Insights
In an era where digital trust is paramount, understanding the inner workings of computing hardware has become as crucial as software security. Enter AMD Privacy View — a powerful, yet underutilized tool designed to demystify sensitive data operations within AMD-based processors. By offering real-time visibility into memory transactions, security states, and hardware-level behaviors, AMD Privacy View empowers users, developers, and security professionals to make informed decisions about privacy and performance.
Unlike generic monitoring tools, it zooms in specifically on AMD platforms, delivering granular insights into how sensitive information flows through memory and processor caches.
Accessible through registered software interfaces or integrated diagnostic dashboards, AMD Privacy View reveals data access patterns invisible to conventional system utilities. This reveals everything from cache side-channel leakage risks to unauthorized memory access attempts — critical data for maintaining confidentiality in multi-tenant environments, cloud computing, and enterprise workloads.
For developers, it serves not only as a debugging aid but also as a privacy compliance checkpoint before deploying applications on AMD hardware.
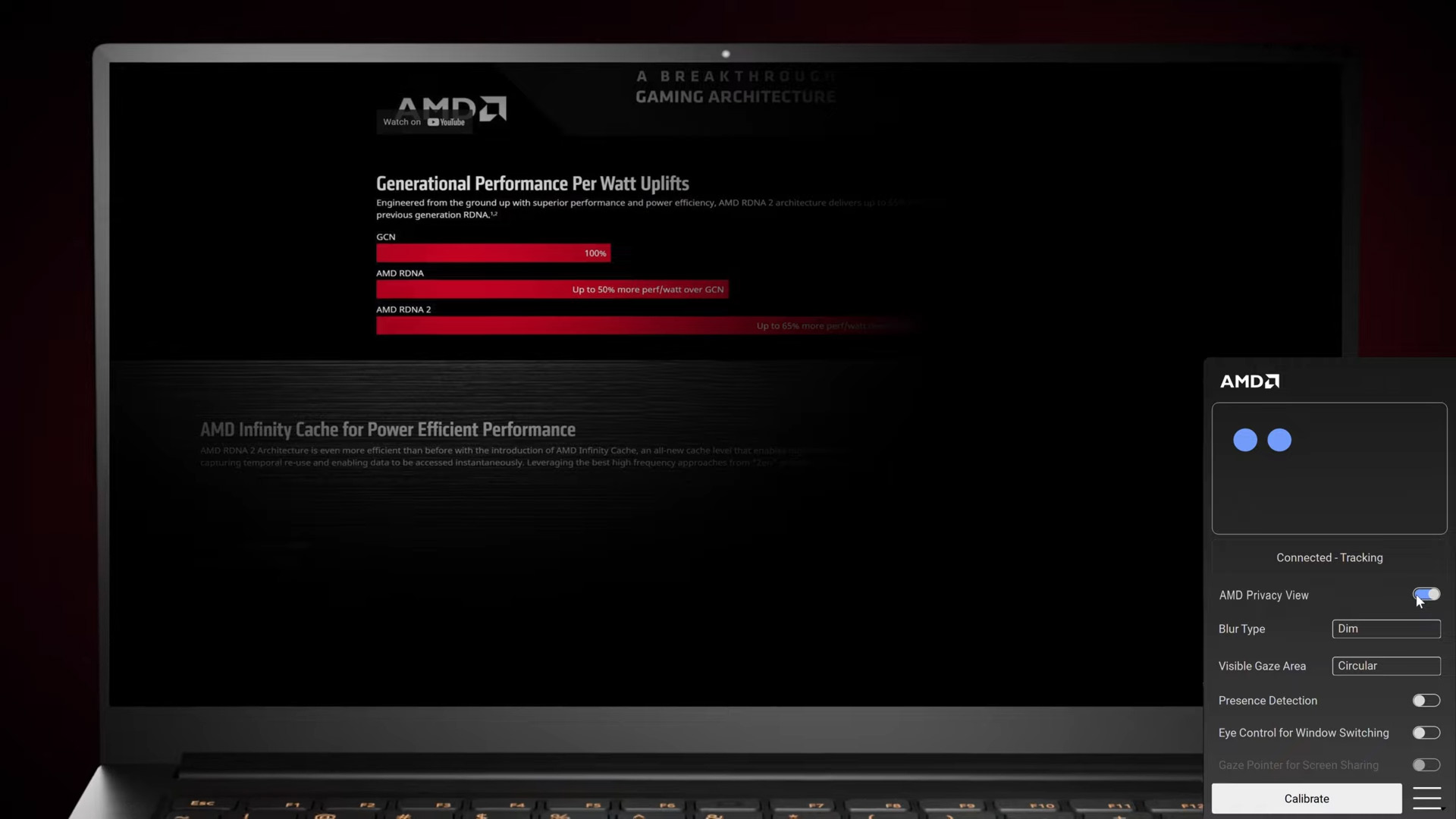
### The Core Functionality Behind AMD Privacy View At its core, AMD Privacy View functions as a real-time monitor for silicized processor activity, focusing on key privacy-critical operations: - **Memory Transaction Tracing**: It tracks reads and writes to RAM, flagging unusual or unauthorized access patterns that may signal side-channel vulnerabilities. - **Security State Visualization**: Users can inspect protection levels such as SME (Secure Memory Encryption) and SMM (Secure Monitor Mode) states, revealing whether confidential computing environments are properly engaged. - **Hardware Interaction Logs**: The tool logs extended telemetry, including cache hit/miss rates and speculative execution behaviors, shedding light on performance-privacy trade-offs.“Privacy isn’t just about data in motion—it’s about knowing what happens in the machine’s memory begins,” explains Dr. Elena Torres, a semiconductor privacy researcher. “AMD Privacy View bridges the gap between abstract security policies and observable hardware behavior, turning theoretical protections into tangible evidence.”
Why AMD-Focused Transparency Matters in Modern Computing
AMD processors power a vast majority of workstations, servers, and edge devices running sensitive workloads—from AI training pipelines to financial analytics.Yet, as side-channel attacks grow more sophisticated, relying solely on software-level safeguards proves insufficient. Hardware itself can leak data through timing discrepancies, cache utilization, or speculative execution—vectors that traditional security audits often miss.
AMD Privacy View addresses this critical blind spot by grounding transparency in the physical layer.
“Software-based tools show you what’s possible on paper, but they don’t reveal what’s happening inside the silicon,” notes Carlos Menezes, a DevOps architect specializing in trustworthy computing. “With AMD Privacy View, we can validate that SME is active, detect anomalous cache behavior, and confirm that vulnerabilities like Spectre or Meltdown are mitigated at the hardware level.”
- **Multi-Tenant and Cloud Workloads**: In cloud infrastructure, where virtual machines share physical cores,Privacy View helps confirm secure memory isolation—preventing cross-tenant data leakage. - **Embedded and IoT Devices**: Devices with minimal software overhead benefit from hardware-level insights without overburdening limited resources.- **DevSecOps Pipelines**: Integrating Privacy View into CI/CD workflows allows teams to audit privacy compliance early, reducing risk exposure in production. One compelling use case involves a financial institution migrating AI workloads to AMD EPYC processors. By deploying Privacy View during testing, engineers identified unintended cache data retention—even after encryption—triggering immediate fixes before deployment.
“We uncovered subtle side effects no manual scan found,” said lead engineer Sofia Reed. “AMD Privacy View didn’t just detect the issue; it gave us actionable visibility.”
Technical Depth: What Payloads Does AMD Privacy View Reveal?
AMD Privacy View operates across multiple visibility layers, each uncovering distinct privacy-relevant facets:- Cache Access Profiling: Detailed logs of L1, L2, and L3 cache interactions reveal how often data is accessed at different levels—flagging potential leakage from speculative loads.
- Memory Encryption States: Real-time monitoring of AMD Secure Memory Encryption (SME) ensures that protected memory regions are genuinely isolated, not merely unencrypted in memory.
- Interrupt and I/O Activity: Insights into how peripherals, drivers, and hyper-threading engage help trace unintended data exposure paths.
- Power and Timing Anomalies: Subtle deviations in CPU behavior linked to timing side channels provide early warnings for attack vectors.
Access, Use, and Implementation Best Practices
Getting started with AMD Privacy View is straightforward for registered stakeholders. The tool is delivered via: - Dedicated diagnostic modules bundled with select system utilities. - Integration with AMD DocuStudio and Partitionallel’s LifePoint Insights.- API-driven telemetry for developers embedding privacy checks directly into software. For optimal use: 1. **Enable Full Visibility Modes**: Ensure SME, SME-compatible memory emulation, and side-channel monitoring are active.
2. **Combine with Hypervisor-Level Tools**: In virtualized environments, correlating Privacy View data with hypervisor logs strengthens isolation validation. 3.
**Schedule Regular Audits**: Use scheduled dashboards to track trend patterns over time—useful for spotting gradual degradation or recurring anomalies. “Many organizations treat hardware telemetry as a peripheral detail,” notes cybersecurity consultant James Wu. “But when paired with AMD Privacy View, it becomes a cornerstone of holistic risk management—especially as regulations demand deeper technical accountability.”
The Future of Privacy at the Silicon Level
As computing advances into AI-driven, heterogeneous architectures, hardware transparency will define privacy resilience.AMD Privacy View exemplifies how specialized tools, rooted


Related Post

) AMD Privacy View: The Transparent Shield Fortifying Socket Ecosystems in Modern Computing

Amd Privacy View: The Revolutionary Camera Feature Redefining Personal Privacy on Linux