Secure Web APIs with Azure AD B2C: Building Enterprise-Grade Authentication and Access Control
Secure Web APIs with Azure AD B2C: Building Enterprise-Grade Authentication and Access Control
In an era where digital identity defines the boundary between secure enterprise systems and cyber exposure, Secure Web APIs powered by Azure Active Directory B2C (Azure AD B2C) have emerged as a cornerstone of modern authentication architecture. Organizations leveraging Azure AD B2C for identity management now face a critical need: integrating secure, scalable, and standards-compliant Web APIs that authenticate users, authorize access, and protect sensitive data—all through a unified identity platform. This comprehensive guide demystifies how secure web APIs work in concert with Azure AD B2C, covering secure design principles, authentication flows, authorization strategies, and best practices that ensure both robust security and seamless user experiences.
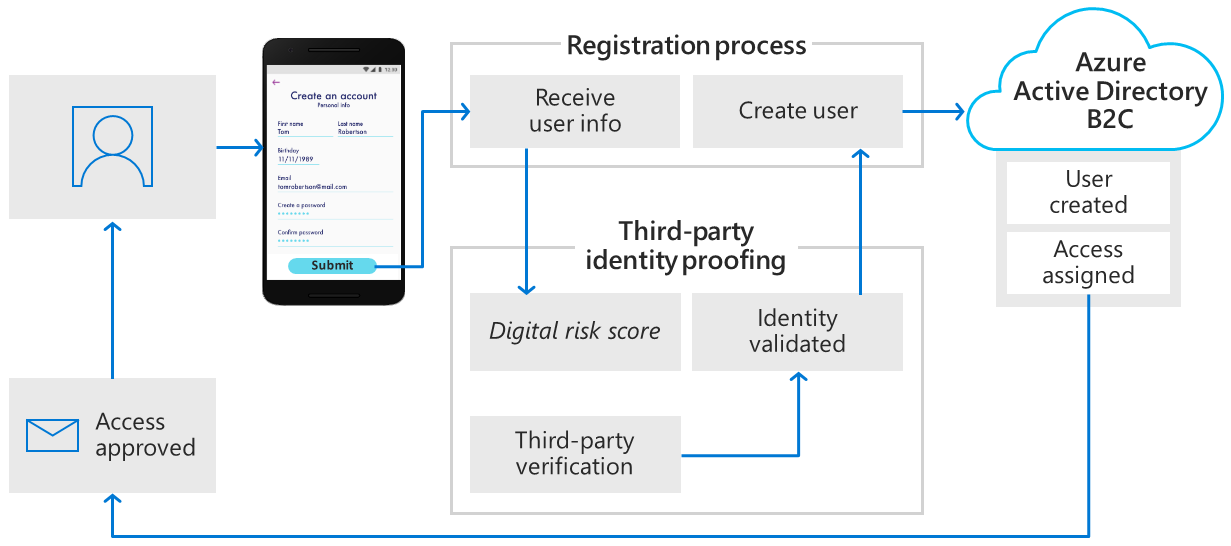
Azure AD B2C delivers a fully managed, identity-as-a-service platform designed to handle high-volume authentication and user lifecycle management without the operational burden of self-managed systems. When paired with Secure Web APIs—typically RESTful endpoints secured through industry standards like OAuth 2.0, OpenID Connect, and JWT (JSON Web Tokens)—organizations unlock granular control over who accesses their applications and data. This integration enables robust identity flows that align with enterprise security requirements and global compliance standards such as GDPR, HIPAA, and CCPA.
The Architecture of Secure Web APIs in Azure AD B2C
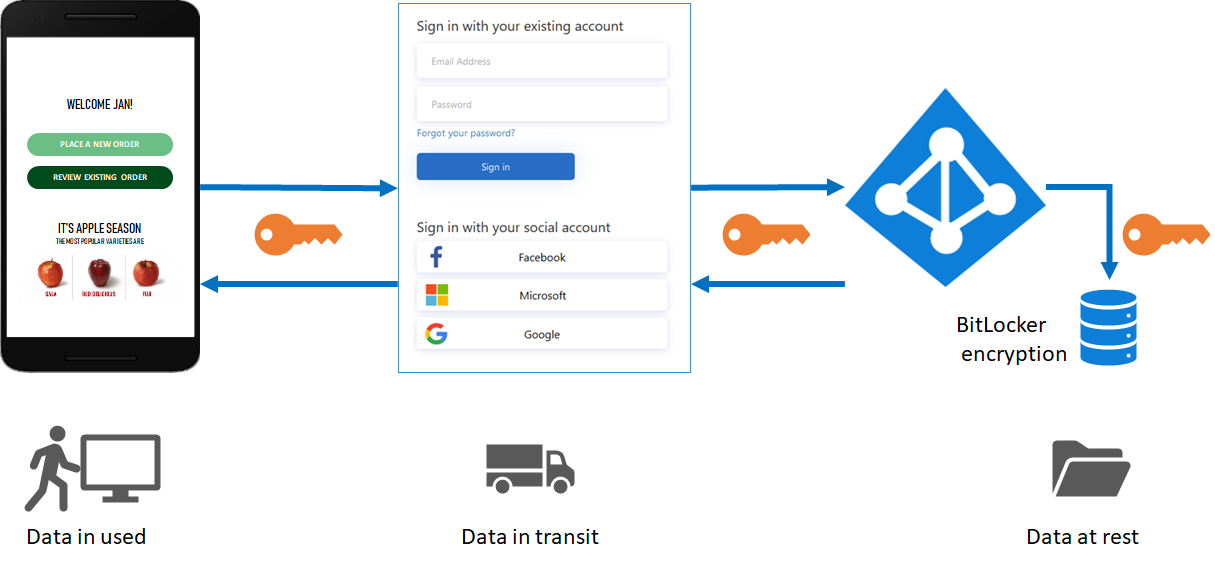
At the heart of Azure AD B2C-powered secure APIs lies a well-defined, layered architecture designed to protect data at rest, in transit, and during processing. The API infrastructure consists of several key components: - **User Authentication Layer:** Implemented through Azure AD B2C sign-in flows, including social identifiers, multi-factor authentication (MFA), and custom identity providers. Each sign-in request is validated against Azure AD B2C metadata, ensuring only authorized users initiate API requests.- **API Gateway:** Acts as the entry point, enforcing HTTPS, rate limiting, and request validation. Using Azure API Management or Azure Front Door, traffic is routed securely, logged, and analyzed for anomalies in real time. - **Token Validation Layer:** Upon successful authentication, Azure AD B2C issues temporally scoped JSON Web Tokens (JWTs), containing user claims and identity attributes.
These tokens are validated in API endpoints via signing key verification and token introspection, ensuring token integrity and expiration checks. - **Authorization Layer:** Leverages Azure Policy, Role-Based Access Control (RBAC), and attribute-based access control (ABAC) to enforce least-privilege principles. Access to API resources is granted only after verifying user roles, consumption contexts, and dynamic claims.
- **Logging & Monitoring:** Embedded observability tools track API usage, authentication success/failure, and token issuance events. Integrating with Microsoft Sentinel or Azure Monitor enables proactive threat detection and forensic analysis. This architecture ensures that every API interaction is authenticated, authorized, and auditable—meeting stringent security and compliance demands.
Authentication Flows: Securing User Sign-In and API Access
Central to Azure AD B2C’s role in secure web APIs are its authentication flows, which govern how users prove their identity before accessing protected resources. Among the most widely adopted flows are: - **Standard Web Authentication (Implicit Flow Adapted):** Designed for single-page applications (SPAs), this flow exchanges an authorization code for an ID token and access token after user consent. Authorization servers redirect users to Azure AD B2C login, validate credentials, and issue tokens upon successful sign-in.- **Client Credentials Flow (Machine-to-Machine):** Enables secure API service access, where backend services authenticate using client ID and secret or certificate, retrieving short-lived tokens to access APIs without user involvement. This flow supports automated workflows and server-to-server interactions. - **Hybrid Identity Flows:** Support seamless transitions between human and service identities, allowing identity providers to federate across on-premises directories and Azure AD B2C.
This flexibility enables unified access across hybrid environments. “A well-implemented authentication flow is the first line of defense in protecting an organization’s digital ecosystem,” notes Microsoft’s identity platform documentation. “Azure AD B2C’s support for adaptive, MFA-enhanced flows ensures that every API request begins with proven, compliant identity validation.” Organizations implementing these flows must enforce strict validation rules, including: - Mandatory MFA for all user sign-ins exceeding predefined risk thresholds.
- Refresh token rotation and short expiration times to reduce token misuse exposure. - Consistent use of Consent APIs to verify user consent and scope of access per API resource.
Authorization and Fine-Grained Access Control
Authentication confirms identity; authorization determines what actions a user or service can perform.In Azure AD B2C-integrated web APIs, authorization is enforced through a combination of token claims, policies, and dynamic evaluations. - **Token-Based Claims:** Azure AD B2C issues rich, verifiable claims including user roles, affiliations, and consent states. APIs validate these claims and map them to authorization policies using Microsoft Identity System or Azure Policy.
- **OPA (Open Policy Agent) Integration:** Advanced scenarios leverage OPA to evaluate access rules dynamically, adding layers of governance based on context such as location, device posture, or data sensitivity. - **Conditional Access Policies:** Tied directly to authentication events, these policies enforce requiring MFA, IP geofencing, or device compliance before allowing API access. Conditional policies reduce risk by responding to real-time threat intelligence.
For example, a healthcare API may permit read access to patient records only when: - The user has the “Provider” role. - Authentication includes verified MFA. - The access request originates from an internal EHR system within secure network boundaries.
“This granularity transforms access control from a static gate to a dynamic, risk-aware gatekeeper,” explains enterprise identity experts. “Azure AD B2C enables organizations to embed contextual security deeply into every API transaction.” Organizations must also maintain clear audit trails of authorization decisions, enabling compliance with data protection regulations.
Secure Data Exchange: Token Validation and API Security Best Practices
Secure Web APIs relying on Azure AD B2C must rigorously validate tokens and enforce secure communication protocols to prevent interception, replay attacks, or data leakage.- **Always Use HTTPS:** All API endpoints require TLS 1.2 or higher. Azure AD B2C tokens are signed and encrypted; transmission over unencrypted channels defeats their security guarantees. - **Validate Token Signature and Issuer:** APIs must verify the JWT signature using Azure AD B2C’s public keys retrieved via well-known discovery endpoints.
Checking the `iss` (issuer) claim ensures tokens originate from trusted Azure AD B2C instances. - **Employ Short-Lived Tokens with Intelligent Refresh:** To minimize exposure, use short-lived ID tokens (headless tokens) at login and enduring refresh tokens with controlled lifespans. Avoid storing refresh tokens in client-side storage; use secure, HttpOnly cookies with SameSite and Secure flags.
- **Throttle and Rate-Limit Requests:** Prevent brute-force attacks by configuring API gateling policies that limit authentication attempts, request volumes, and token refresh rates. Azure API Management offers built-in rate-limiting features tailored to B2C workflows. - **Sanitize and Validate Input Data:** Even authenticated users are vulnerable to injection attacks.
Always validate, sanitize, and authorize on every request based on the principle of least privilege. - **Enable Runtime Threat Detection:** Use Azure Sentinel to correlate login anomalies, unusual API usage patterns, and credential stuffing alerts for immediate response. Microsoft’s architecture best practice guidance emphasizes that “token validation is not a one-time act—it is a continuous process embedded in every request lifecycle.” This layered validation ensures that even if a token is intercepted, its lifespan and scope limit its abuse potential.
Real-World Use Cases: Deploying Secure APIs in Diverse Environments
Organizations across sectors are adopting Azure AD B2C with Secure Web APIs to modernize identity and authorization. In healthcare, APIs integrated with Azure AD B2C enable interoperable patient data exchange between providers, payers, and EHR systems—ensuring HIPAA compliance while supporting secure API-driven workflows. In finance, banks deploy OAuth 2.0-based API gateways with Azure AD B2C to offer secure account aggregators and third-party fintech integrations, where OAuth scopes and consent snapshots regulate data shared across platforms.Enterprises migrating to the cloud leverage Azure AD B2C APIs to unify identity across SaaS applications—enabling single sign-on (SSO), multi-factor authentication enforcement, and role-based data access without branching internally managed identity databases. One notable case involves a global software provider that re-architected its customer portal APIs using Azure AD B2C. By embedding JWT validation, OPA-Atlas policies, and real-time threat detection, the company reduced authentication fraud by 78% and achieved SOC 2 Type II certification more efficiently.
“Secure API design with Azure AD B2C isn’t about adding layers—it’s about embedding trust into every interaction,” states a lead architect from the organization. “It turns identity into a strategic asset, not just a compliance checkbox.” Another example: a large retail chain implemented Azure AD B2C-powered APIs for its loyalty program. Each customer API call after authentication includes consent attributes encoded in the token, ensuring GDPR-compliant data access while personalizing user experiences at scale.
Future-Proofing Identity: Extending Azure AD B2C Security
As cyber threats grow in sophistication, secure web API strategies must evolve dynamically. Azure AD B2C continues to

Related Post

Iirkoll: Decoding a Symbol Shaped by Meaning and Cultural Resonance

Microsoft Solitaire Collection: The Ultimate Digital Card Game Experience in One Pack

Netflix vs. Traditional TV: Who Starts the Binge War?

One Above All: The Relentless Principle Shaping Strategy, Leadership, and Purpose

