PM SVANidhi EKYC Guide: Your Step-by-Step Roadmap to Seamless Digital Identity Verification
PM SVANidhi EKYC Guide: Your Step-by-Step Roadmap to Seamless Digital Identity Verification
In an era where digital transactions demand speed, security, and trust, mastering the EKYC (Electronic Know Your Customer) process is no longer optional—it’s essential. The PM SVANidhi EKYC Guide delivers a clear, practical framework to navigate India’s evolving digital identity verification landscape with confidence. Whether you’re a fintech entrepreneur, bank employee, or individual setting up digital accounts, this step-by-step tutorial demystifies EKYC procedures, ensuring compliance while streamlining onboarding.
With straightforward instructions and real-world examples, anyone can complete the process efficiently—no legal jargon, no technical confusion, just execution.
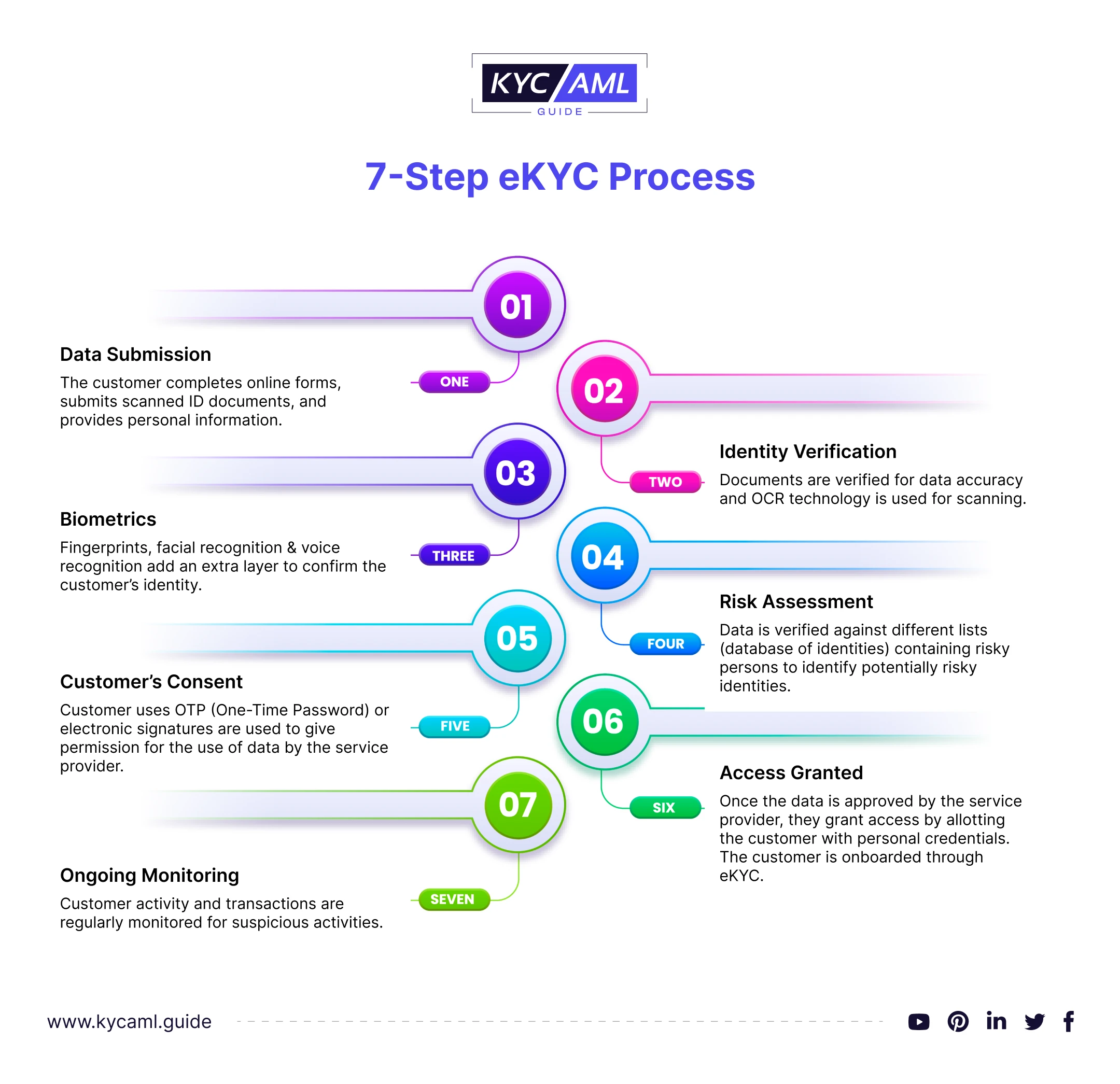
At the heart of PM SVANidhi EKYC Guide lies a structured, user-centric methodology designed to fit both tech-savvy and non-technical users. The process integrates government mandates with industry best practices, offering a reliable path through identity proof, proof of address, and risk assessment.
This guide ensures you meet regulatory standards while maintaining a smooth user experience—critical in a market where user trust directly impacts adoption rates.
Step 1: Gather Required Documents with Precision
The first pillar of a successful EKYC lies in meticulous documentation. BMISPVANidhi emphasizes that incomplete or incorrect paperwork halts verification and damages credibility. The template list of required documents is comprehensive and precise: - Valid government-issued photo ID (Aadhaar, PAN, voter ID, or passport) - Recent utility bill, bank statement, or government document as proof of address - Cross-verified photograph matching identity documents - Passport-size passport-sized picture compliant with Byte Protocol or SVANidhi guidelines - Any additional documents based on risk classification—such as business registration for fintech clients “Lack of proper documentation is the most common bottleneck,” notes EKYC compliance expert Dr.Ananya Mehta. “Verification teams reject 30–40% of applications due to missing or mismatched details. Preparation is your first line of defense.”
Organize documents in advance: digital scans or high-resolution photos clear of glare and zoom.
Avoid scanned copies with watermarks, and ensure IDs are unexpired—policies strictly enforce this to prevent fraud. The guide stresses scanning IDs at 300 DPI with front-and-back views to facilitate automated facial recognition and data extraction.
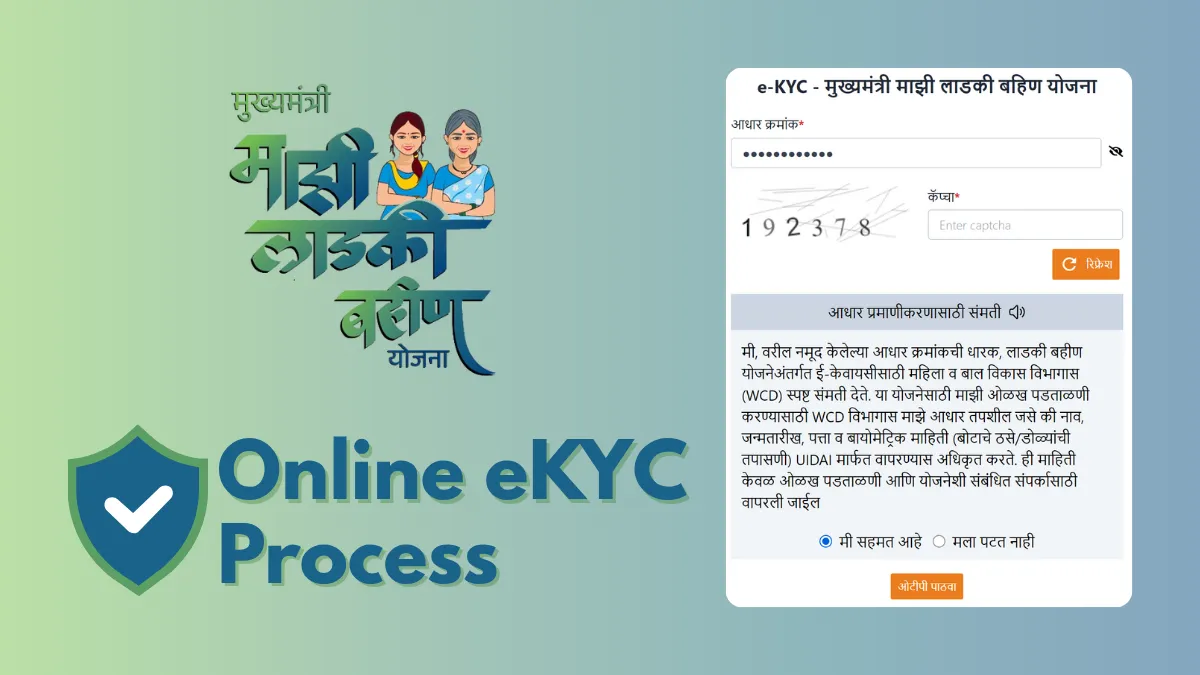
Step 2: Initiate Verification via Authorized EKYC Platforms
Once documents are ready, next is selecting a certified EKYC service provider. Under PM SVANidhi’s framework, this step is optimized for security and compliance.Only registered platforms authorized by the Ministry of Electronics and IT (MeitY) should be used, as they meet Data Protection Act standards and integrate with Aadhaar’s OTP-based authentication. The guide highlights three primary platforms: - UIDAI’s e-Sewa portal for government-issued identities - Third-party fintech EKYC aggregators offering AI-driven verification - Blockchain-based identity networks for high-risk or cross-border onboarding “We recommend vetting platforms based on response time, error rates, and compliance certifications,” advises SVANidhi’s validation team. “Every verification requires a unique device IP log and biometric check—non-negotiable security layers.”
Most systems prompt users to initiate verification through UPI-linked accounts or saved mobile numbers.
On the platform, you’ll submit documents, confirm identity details, and trigger automated checks against Aadhaar, PAN, and watchlists. Real-time dashboards update status from submission to approval, reducing guesswork.
Step 3: Facial Recognition and Liveness Detection
Modern EKYC processes integrate biometric verification to confirm identity match and prevent impersonation. The PM SVANidhi EKYC Guide underscores that facial recognition is now a regulatory frontier—failed matches can trigger manual intervention, delaying verification.Step-by-step, the process works as follows: - A high-res photo is captured via smartphone camera, separated from background using AI masking - Deep learning algorithms


Related Post
Kenny Smith NBA Bio Wiki Age Height Wife Kids Salary and Net Worth

Joshua Ledet Wife Age: Discovering the Personal Life Behind the American Idol Star

