10.0.0.0.1/Admin: The Command Center Accessing Critical Infrastructure
10.0.0.0.1/Admin: The Command Center Accessing Critical Infrastructure
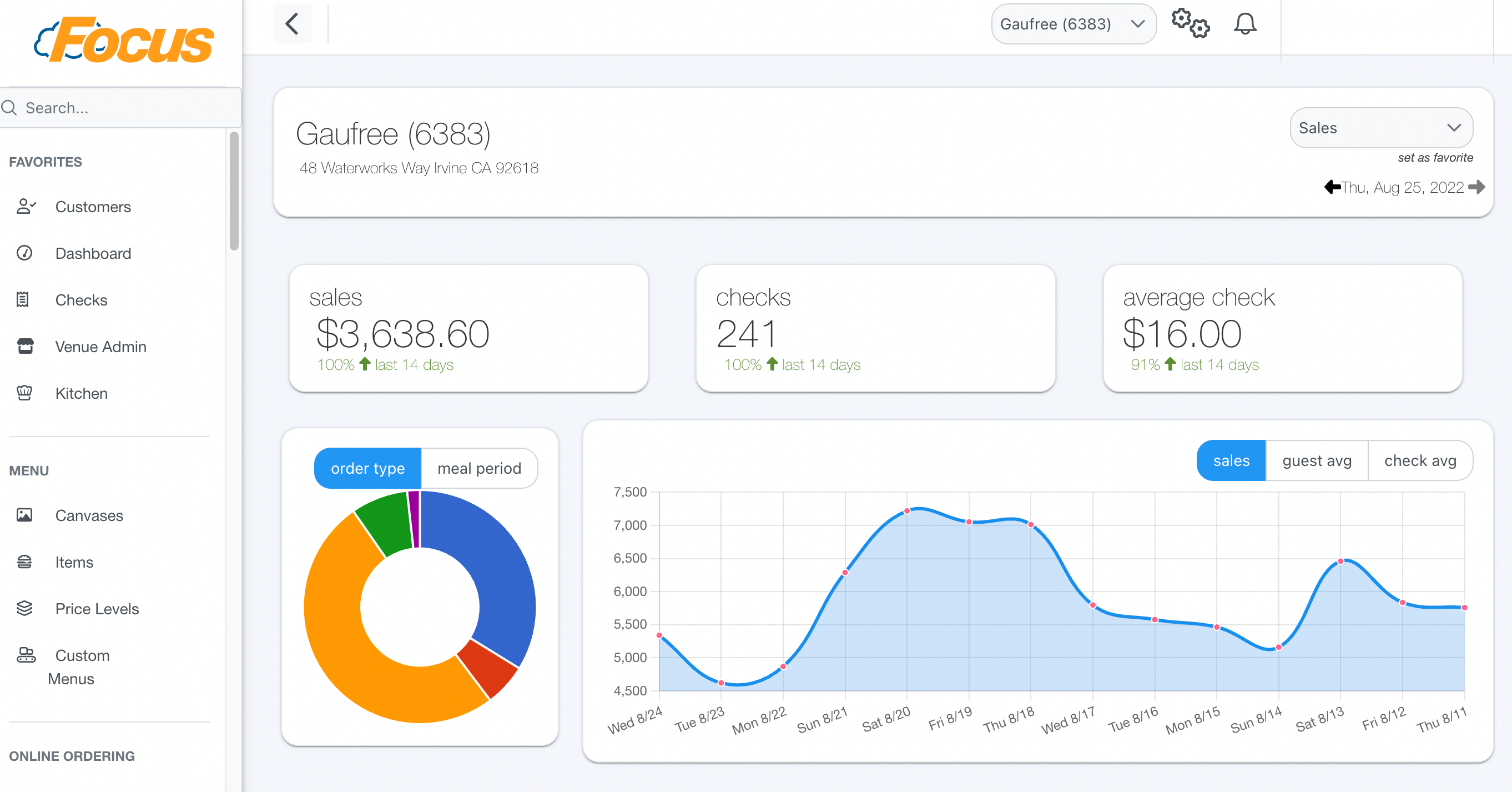
At the core of modern network management lies a vital IP address: 10.0.0.1/Admin. This is not merely a designator in a routing table, but the primary gateway to centralized system administration for enterprise-grade networks, industrial control systems, and cloud infrastructure. Serving as the control node for privileged access, 10.0.0.1/Admin enables system administrators to monitor, configure, monitor, and secure complex digital ecosystems.
As organizations increasingly depend on seamless connectivity and operational resilience, understanding this critical access point reveals both its technical significance and strategic importance in today’s digital backbone. Understanding the IP Crypt: What Does 10.0.0.1/Admin Represent? The IP address 10.0.0.1/Admin follows a structured format used in IPv4 addressing, where the prefix “/Admin” signifies more than a network segment—it denotes administrative functionality.
In enterprise environments, IP ranges like 10.0.0.0 to 10.255.255.255 are reserved for private networks, commonly deployed in internal systems and management interfaces. The “/Admin” at the end is not part of the IP itself but a convention indicating this is the endpoint for privileged commands, dashboards, or configuration tools. This address acts as the primary gateway through which users log in to manage firewalls, routers, network monitoring, and access controls.
> “Accessing 10.0.0.1/Admin is the first and most secure step in managing any organization’s digital infrastructure,” notes a network security expert from a leading IT firm. “Architecturally, it sits at the intersection of network reachability and privileged governance—like the pulse point of enterprise IT.” This blend of accessibility and exclusivity makes 10.0.0.1/Admin a linchpin of cybersecurity architecture and operational continuity.
Core Functions Powered Through 10.0.0.1/Admin
Accessing the 10.0.0.1/Admin interface unlocks a suite of essential administrative capabilities designed to maintain, audit, and optimize digital assets.Key functions include: - **System Configuration Management**: From firewall rules to interface priorities, admins configure network behavior through intuitive, role-based dashboards accessible via 10.0.0.1/Admin. - **Real-Time Monitoring & Alerting**: Continuous tracking of bandwidth usage, device status, and traffic anomalies enables proactive issue resolution before outages occur. - **User Access & Role Control**: Granular permission tiers allow administrators to define who can manage systems, what levels of access they possess, and when changes are permitted.
- **Security Policy Enforcement**: Centralized deployment of encryption standards, intrusion detection settings, and compliance checks ensures adherence to internal and regulatory frameworks. - **Remote Troubleshooting & Maintenance**: With SSH and CLI interfaces accessible through 10.0.0.1/Admin, engineers can diagnose and resolve hardware/software anomalies without physical site access. Each function reinforces system stability, agility, and defensibility—critical in environments demanding zero-downtime operations.
Security Considerations for Accessing 10.0.0.1/Admin
Despite its operational centrality, exposing 10.0.0.1/Admin without proper safeguards invites serious risk. As a high-value entry point, this admin interface is a prime target for cyber threats including brute-force attacks, credential stuffing, and man-in-the-middle exploits. Enterprises must implement robust protective measures: - **Strong Authentication**: Multi-factor authentication (MFA) is non-negotiable.Even a single compromised credential can grant attackers full network control. - **Role-Based Access Control (RBAC)**: Limit administrative privileges based on job function and necessity to minimize internal and external attack surfaces. - **Network Segmentation**: Isolate the 10.0.0.1/Admin subnet from public-facing networks.
Use firewalls and DMZ placements to reduce exposure. - **Regular Patching and Updates**: Ensure the OS, firmware, and underlying software powering 10.0.0.1/Admin are current against known vulnerabilities. - **Audit Logging & Anomaly Detection**: Enable comprehensive logging of login attempts, configuration changes, and API calls to detect suspicious behavior instantly.
Standard cybersecurity best practices must be rigorously enforced. According to a 2023 report from the Cybersecurity and Infrastructure Security Agency (CISA), networks without enforced access controls at critical control points experience 68% more successful intrusions than those with layered protections in place.
Best Practices for Administering Access to 10.0.0.1/Admin
Effective administration of the 10.0.0.1/Admin interface demands a disciplined, proactive approach that balances usability with security.Key operational recommendations include: - **Access via Encrypted Channels Only**: Configure access exclusively through HTTPS (with valid SSL certificates) and SSH tunnels to prevent data interception. - **Maintain Least Privilege Principle**: Grant only the minimal permissions required for each user, reducing the risk of accidental or malicious misuse. - **Implement Configuration Backups and Version Control**: Track every change with timestamped audit trails to support rollback and forensic analysis.
- **Schedule Regular Security Reviews**: Conduct quarterly assessments of access logs, authentication policies, and role assignments to adapt to evolving threats. - **Integrate with Identity Providers (IdPs)**: Leverage LDAP, Active Directory, or cloud IAM solutions to streamline authentication and reduce password fatigue. These strategies ensure operational efficiency remains aligned with strong governance, enabling administrators to act decisively while safeguarding the network’s integrity.
The 10.0.0.1/Admin interface is far more than a login page—it is the operational nerve center where control, security, and innovation converge in modern infrastructure. Its proper use enables responsive, secure management across vast digital ecosystems, while mismanagement opens doors to systemic risk.
As organizations rapidly expand cloud-first models and edge computing, the role of centralized admin gateways like 10.0.0.1/Admin will only grow. Future readiness demands not just access—but intelligent, adaptive administration.
Enterprises that treat this IP as a strategic asset—protecting it with rigor and leveraging it with precision—will maintain competitive advantage, reliability, and trust in an era where digital resilience defines success.


Related Post
Guy Benson Fox News Radio Bio wiki Age Husband Book Salary And Net Worth

Bloxclaim: The Emerging Force Redefining Digital Claims Validation in Game Ecosystems
WWE Nixed Big Plans For Bray Wyatt WrestleMania Entrance

